The past two years have been centered around accelerating digital transformation. Now, the pendulum has swung the other way, with governance forcing companies to revisit and address security protections that were overlooked during the rapid changes of the pandemic.
For many midmarket information technology (IT) leaders, security needs to catch up. But it's not just about catching up. It's time to recalibrate the relationship between security and digital transformation and put security back into an active role.
Why the balance between innovation and security has shifted
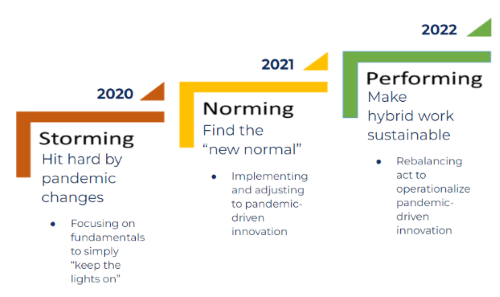 Image courtesy of Barbour
Image courtesy of Barbour
Since 2020, necessity has driven digital transformation. COVID-19 demanded new business models and created a “storm” of change. Instead of closing their doors, executives had no choice but to put cybersecurity considerations on the back burner and mobilize guerilla IT to keep things running. Hastily ordered solutions created new risks.
- Remote Work: Cost and supply chain constraints meant that personal devices were sometimes used for work, creating an unmanaged environment and expanding the attack surface for businesses.
- employee: Security awareness training often fails as employee turnover is on the rise, and while it's difficult to pinpoint the root cause of attacks, the 150% increase in ransomware attacks and its connection to unpatched endpoints and untrained users cannot be overlooked.
- cloud: Security has become more complex due to concerns about shadow IT, misconfigurations of cloud applications, and changing security roles and responsibilities as services move to the cloud.
After the “standardize and execute” phase of 2021 and 2022, mid-sized businesses are now looking to fill the gaps left in the wake of rapid change.
A dangerous but necessary game of catch-up
A backlash often occurs when innovation outpaces security. The effect can be described as security “putting the brakes” on transformation. In the worst-case scenario, companies put the brakes on after a security breach or ransomware incident, but more often than not, they do so after concerned stakeholders ask for a security risk assessment. Either way, steps are taken to assess risk, manage exposure, and put controls in place. Several studies highlight the resurgence of security today.
-
76% of CIOs say it's difficult to find the right balance between business innovation and operational excellence.
- “After scrambling to adapt to the disruption caused by the pandemic, security teams are deploying and managing technologies and processes to build security into web and mobile applications, make remote work safe, and improve the security and economics of networks and cloud-based resources,” ISC said.2 report.
- Gartner analysts also describe cloud security challenges: “The most commonly cited challenge to cloud adoption is gaining security team buy-in and support for the cloud migration strategy, suggesting that security teams are struggling to adapt to the increasing complexity of cloud technologies.”
Playing catch up can be costly for businesses. If a remote worker is the cause of a data breach, costs increase by $1.07 million, totaling $5.31 million on average. Businesses may have to take on everything at once, updating security while simultaneously paying ransomware attackers and emergency response teams. For these reasons, playing catch up is considered a risky game, but IT executives shouldn't feel blamed or stressed. COVID-19 has left them with no choice. Correcting course now, before a data breach occurs, is still an honorable victory.
How do we establish checks and balances?
If your organization doesn't already have a formal security program, start with these steps:
- Reassess security for remote work: Yesterday's stop-gap measures remain a long-term strategy when employees use their own devices to work outside defined boundaries.
- Start your cyber risk assessment. Identify priorities based on risks and business objectives to know where to focus now and in the future.
- If your organization has more than a few hundred employees, it needs at least one dedicated security resource empowered to challenge reckless behavior. Without an authorized owner, business decisions will ignore risk mitigation and your security program will likely never get off the ground.
- Combined with a risk assessment, use available cybersecurity frameworks to identify necessary controls and practices. Prioritize and act with a sense of urgency. Don't expect to do everything at once.
Rebalancing security and innovation
Ideally, security shouldn't keep up with innovation, but should be in sync with or even ahead of business strategy. Now is the time to realign.
You need a process that ensures security and innovation always work hand in hand. Here's how to restore balance:
- Strengthen your security capabilities now and align your security strategy to meet future needs. Think about what your business vision is and how security can enhance it. Think about changes in your users, services, and IT footprint. Put controls in place before you need them to accelerate revenue instead of slow it down.
- Let's start with the familiar trilogy: technology, expertise, and process. While security is primarily about expertise and process, technologies like Cloud Access Security Brokers (CASBs) and Secure Access Service Edges (SASEs) can help restore balance and increase agility by addressing the connectivity and cybersecurity that supports a hybrid workforce. Seek help from security consultants and service providers who can scale your efforts.
- Don’t forget to get executive support. Brief them about the threat landscape relevant to your organization. A proactive approach will accelerate new revenue streams and reduce costs by proactively managing cyber risks as your company tackles new services, markets and users. Of course, there will be a cost, but the alternative is to put the brakes on innovation or pay the price of a data breach.
Leverage security to prepare for the future
Change is certain, and digital transformation is necessary for businesses to continually adapt and take advantage of new market environments. But when security is out of balance, innovation can easily become a disaster. Future-proofing confidence comes from security preparation, management, and enabling rapid change, which are necessary to counter any kind of transformation risk. The key is to have smoke detectors, fire doors, and sprinkler systems, in addition to fire inspectors and specialized alarm monitors. Don't call the fire engine when the house is already on fire.

